Protect and Comply With VAPT
At CyberImmune, we offer robust Vulnerability Assessment and Penetration Testing (VAPT) services to identify, analyze, and help remediate security vulnerabilities across your digital assets.
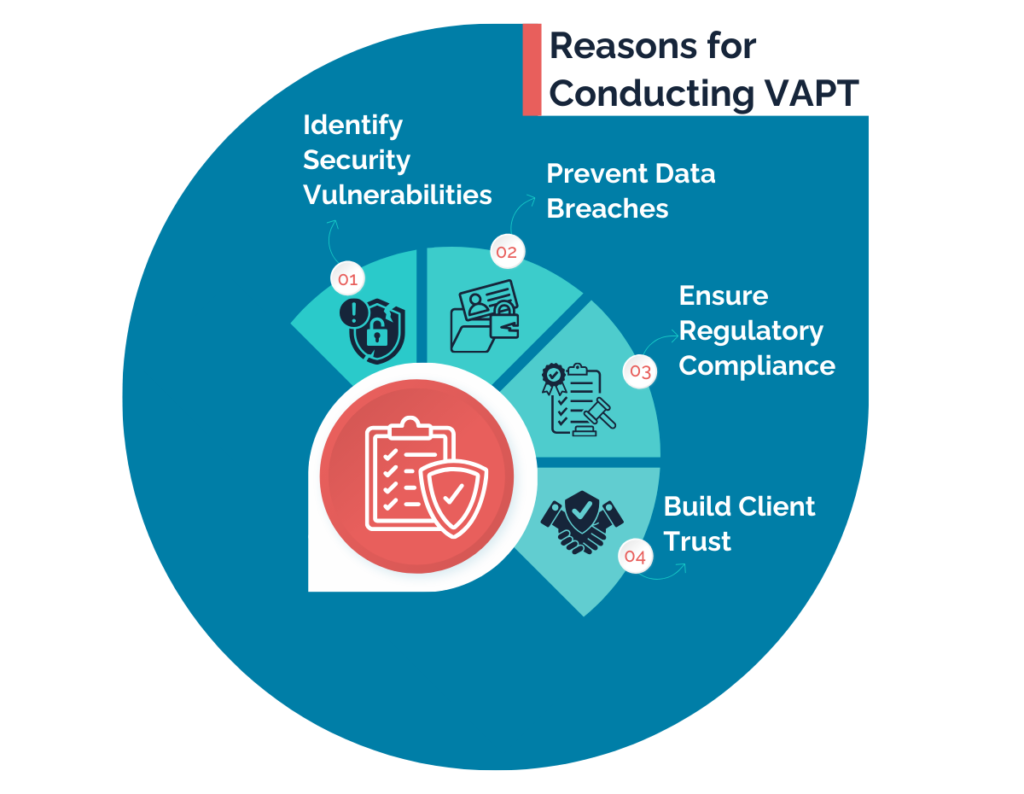
What We Test
Our vulnerability assessment and penetration testing (VAPT) services includes testing of various applications, network, infrastructure to safeguard your business from evolving threats.
Web Applications
Uncover vulnerabilities through both automated scanning tools and manual testing to ensure thorough coverage.
Mobile Applications
Secure iOS and Android mobile applications by uncovering security gaps and ensuring user data safety.
Desktop Applications
Secure your patient data without worrying about attackers stealing information.
OT/ICT
Secure your SaaS applications and increase trust among customers and stakeholders.
Cloud Infrastructure
Secure your SaaS applications and increase trust among customers and stakeholders.
Network Security
Secure your SaaS applications and increase trust among customers and stakeholders.
Our Approach To Vulnerability Management
Our comprehensive Vulnerability Management service ensures that security weaknesses are systematically and continuously identified, evaluated, treated, and reported on.

Continuous Scanning and Discovery
Continuous scanning and real-time asset discovery ensure your IT infrastructure is fully monitored, with seamless integration into existing tools.
Prioritization and Risk Assessment
AI-driven analysis to prioritize vulnerabilities based on impact, business context, and risk, aligned with industry-standard scoring systems like CVSS.
Remediation Planning and Guidance
Receive detailed remediation plans, strategic roadmaps, and ongoing support to ensure vulnerabilities are addressed effectively and on time.
Reporting and Metrics
Get real-time visibility and clear communication of your vulnerability status through custom dashboards, trend analysis, and executive reports.

Third-Party and Supply Chain Risk Management
Assess vulnerabilities from third-party vendors and components with continuous monitoring of your extended digital ecosystem.

Compliance Mapping
Align vulnerability management activities with compliance requirements while supporting audit preparation and reporting processes effectively.

Continuous Improvement
Regularly refine vulnerability management processes by incorporating threat intelligence to address emerging risks proactively and efficiently.
Why Choose CyberImmune?
Tailored Methodologies
Customized VAPT strategies tackling organizational risks and vulnerabilities.
Comprehensive Reporting
Reports include vulnerabilities, remediation steps, improving security posture.
Specialized Expertise
Expert penetration testing for OT, ICT, AI, and applications.
Global Expertise
VAPT services tailored to global and regional needs.
Remediation Guidance
Supporting clients fixing vulnerabilities, strengthening their security posture.
Continuous Improvement
Updated tools and skills counter evolving threats effectively.
VAPT Tools and Technologies We Use
Our team of experts use the latest professional platforms and tools to perform the penetration tests and to secure your applications, network and cloud from all evolving threats.
Network Vulnerability Scanners
- Nessus Professional
- Qualys Vulnerability Management
- OpenVAS
Web Application Scanners
- BurpSuite Professional
- Acunetix
- OWASP ZAP
Mobile Application Testing Tools
- MobSF (Mobile Security Framework)
- Drozer (for Android)
- idb (for iOS)
Database Security Scanners
- AppDetectivePRO
- DbProtect
API Testing Tools
- Postman
- SoapUI
- Insomnia
OT/ICS Security Tools
- Nmap NSE Scripts for ICS
- Shodan
- Dragos Platform
Cloud Security Tools
- Scout Suite (for AWS, Azure, GCP)
- CloudSploit
- Prowler (for AWS)
AI/ML Security Tools
- MLSec
- AI Fairness 360
- Adversarial Robustness Toolbox
Password Cracking Tools
- John the Ripper
- Hashcat
Penetration Testing Frameworks
- Metasploit Framework
- Cobalt Strike
- PowerShell Empire
Wireless Network Testing
- Aircrack-ng
- Kismet
Network Protocol Analyzers
- Wireshark
- tcpdump
Frequently Asked Questions
What is VAPT and why is it important?
VAPT stands for Vulnerability Assessment and Penetration Testing. It's crucial for identifying security weaknesses in your systems before malicious actors can exploit them, helping you proactively strengthen your security posture.
How often should we conduct VAPT?
We recommend conducting VAPT at least annually, or after any significant changes to your infrastructure or applications. For high-risk environments, more frequent testing may be necessary.
How long does a typical VAPT engagement take?
The duration varies based on the scope and complexity of your environment. A basic web application test might take a week, while a comprehensive assessment of a large network could take several weeks.
Will VAPT disrupt our normal operations?
We design our tests to minimize disruption. Most assessments can be conducted without impacting your operations. For more invasive tests, we'll coordinate with your team to schedule them during off-hours.
What deliverables can we expect from a VAPT engagement?
You'll receive a comprehensive report detailing found vulnerabilities, their potential impact, and prioritized remediation recommendations. We also provide an executive summary for management.
How do you ensure the security of our data during testing?
We follow strict security protocols and confidentiality agreements. All testing is conducted by vetted professionals, and any sensitive data encountered is handled according to agreed-upon procedures.
Do you provide remediation support after the VAPT?
Yes, we offer post-assessment support to help interpret results and guide your team through the remediation process. We can also conduct re-testing to verify that vulnerabilities have been properly addressed.
Can you test our cloud-based infrastructure?
Yes, we have expertise in testing cloud environments across major providers like AWS, Azure, and Google Cloud Platform, ensuring your cloud-based assets are also secured.
What certifications do your VAPT professionals hold?
Our team includes professionals with certifications such as CEH, OSCP, CISSP, and other relevant industry qualifications. We ensure our team's skills are always up-to-date.
