Protect, Monitor, and Fortify Your Network
From on-premise systems to cloud network security, our tailored comprehensive network and security solutions safeguard your infrastructure, detect threats, and ensure uninterrupted operations.
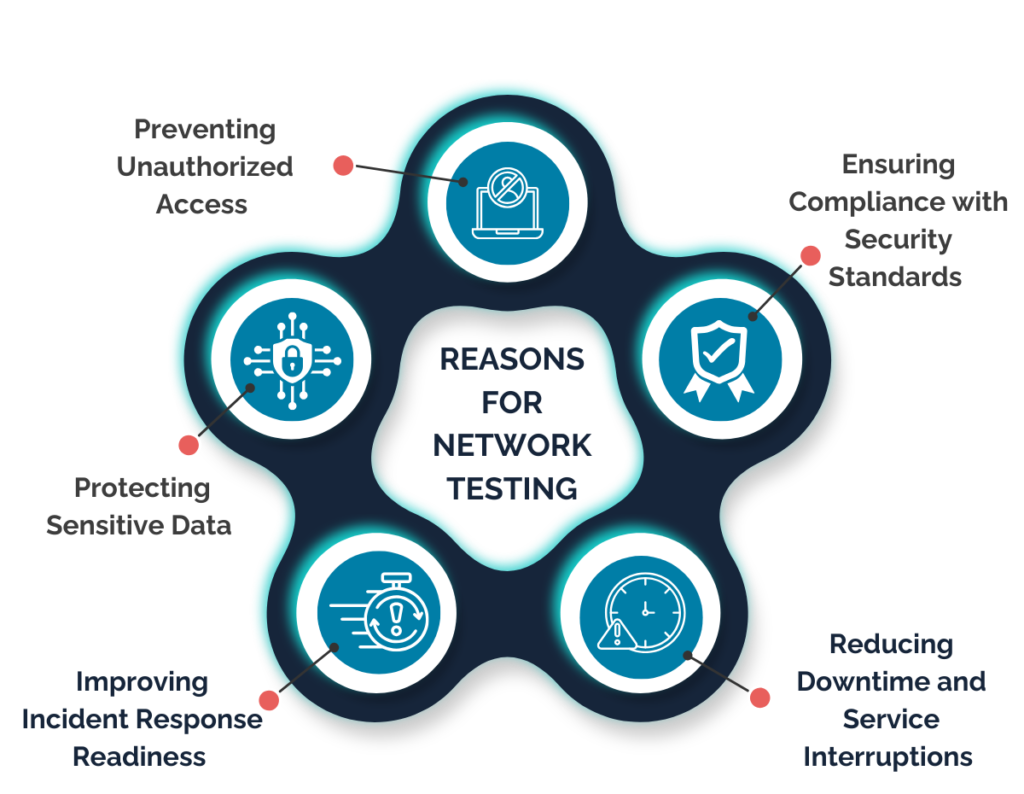
Our Network Security Services
Prevent threat actors, malware, and malicious files from infiltrating and compromising your network.
Network Security Toolkit Deployment
Advanced and innovative tools to efficiently monitor, secure, and manage network traffic effectively.
Network Security Through Red Team
Simulating real-world cyber attacks as an attacker against the network and test your security posture.
Network Monitoring and Reporting
Real-time monitoring and detailed reporting to provide visibility into the network and security performance.
Network Firewall Security
Implementation and management of firewalls to protect against unauthorized access and ensure regulatory compliance.
Network Pen Testing
Identify and fix weak points in the network before they are exploited by malicious threat actors.
Cloud Network Security
Tailored solutions to secure the cloud environments, preventing misconfigurations and data breaches.
How CyberImmune Secures Your Network
Our comprehensive Vulnerability Management service ensures that security weaknesses are systematically and continuously identified, evaluated, treated, and reported on.

Network Security Assessment
We analyze your existing network and security posture to identify vulnerabilities, weak points, and gaps.
Tailored Security Roadmap
Our experts create a clear, customized strategy, deploying tools from our advanced network security toolkit to secure your organization.

Firewall and Intrusion Prevention
We implement network firewall security and intrusion detection systems to monitor, block, and prevent malicious activity in real time.
Cloud Network Security
Secure your cloud infrastructure by implementing best practices, configuration reviews, and ongoing monitoring to protect hybrid and multi-cloud environments.

Continuous Monitoring and Threat Detection
Our 24/7 monitoring identifies unusual activity across your network and security layers, allowing us to detect and respond to threats instantly.
Why Choose CyberImmune?
Customized Solutions
Our services are tailored to your unique infrastructure and business needs.
Comprehensive Reporting
Reports include vulnerabilities, remediation steps, improving security posture.
Proactive Threat Management
Our team identifies risks before they become incidents, combining real-time monitoring with advanced tools for network security.
Expert Team
Our experienced team leverages the latest network security toolkit and industry best practices to deliver robust solutions.
Remediation Guidance
Supporting clients fixing vulnerabilities, strengthening their security posture.
Compliance Ready
We help your business ensure data security compliance across networks.
Our Network Security Toolkit
Our team of experts use the latest professional platforms and tools to perform the penetration tests and to secure your applications, network and cloud from all evolving threats.
Network Vulnerability Scanners
- Nessus Professional
- Qualys Vulnerability Management
- OpenVAS
OT/ICS Security Tools
- Nmap NSE Scripts for ICS
- Shodan
- Dragos Platform
Cloud Security Tools
- Scout Suite (for AWS, Azure, GCP)
- CloudSploit
- Prowler (for AWS)
AI/ML Security Tools
- MLSec
- AI Fairness 360
- Adversarial Robustness Toolbox
Password Cracking Tools
- John the Ripper
- Hashcat
Wireless Network Testing
- Aircrack-ng
- Kismet
Compliance Checking Tools
- OpenSCAP
- Lynis
Exploitation Tools
- ExploitDB
- Canvas
Frequently Asked Questions
What is network security, and why is it important for my business?
Network security protects your IT infrastructure, systems, and data from unauthorized access, cyberattacks, and disruptions, ensuring business continuity and data integrity.
What are the key components of network security solutions?
Key components include firewalls, intrusion detection and prevention systems (IDPS), network monitoring, access control, vulnerability assessments, and secure cloud network configurations.
How can network security prevent cyber threats like malware and ransomware?
Network security solutions block malicious files, unauthorized access, and suspicious activities through firewalls, real-time monitoring, and threat detection tools.
What is the difference between network firewall security and intrusion prevention systems (IDPS)?
Firewalls control access to your network, while IDPS actively monitor, detect, and prevent malicious activities within your network environment.
How does CyberImmune secure cloud network infrastructures?
We perform cloud penetration testing, configuration reviews (CSPM), and continuous monitoring to identify vulnerabilities and secure your cloud-based networks.
How often should my business perform a network security assessment?
We recommend quarterly assessments, after major changes to your infrastructure, or when deploying new tools and services to maintain security.
What is the role of Zero Trust in network security?
Zero Trust ensures that no device or user is trusted by default, enforcing strict access controls and verification across your entire network.
Can CyberImmune monitor my network 24/7 for threats and vulnerabilities?
Yes, our network security services include real-time monitoring and proactive threat detection to ensure continuous protection.
What compliance standards does your network security service align with?
Our services align with standards like ISO 27001, SOC 2, GDPR, HIPAA, and NIST to meet your industry and regulatory requirements.
How do I know my network is secure after implementing your solutions?
We provide detailed reports, and ongoing monitoring to ensure your network security remains strong and effective against evolving threats.
