Secure Your Cloud and Apps with Confidence
Whether your applications are hosted on-prem, or in public, private, or hybrid cloud environments, CyberImmune delivers tailored strategies to safeguard your applications. Our comprehensive cloud application security services ensure your systems remain protected, compliant, and resilient against evolving cyber threats.
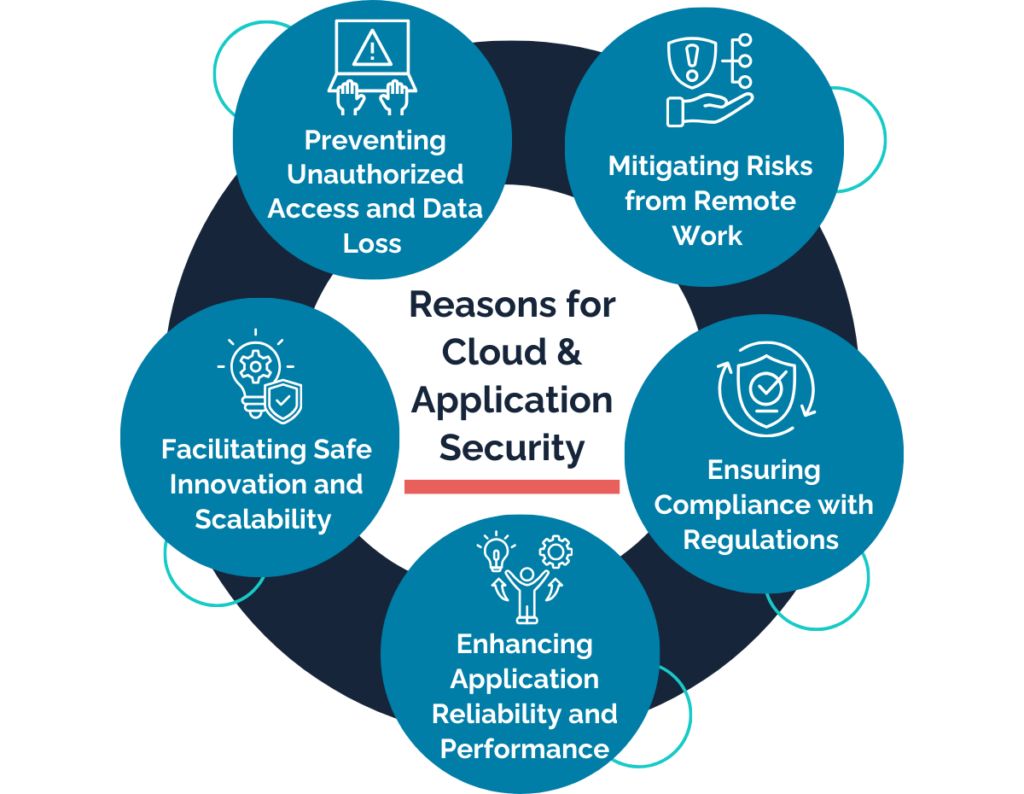
Our Cloud Sec and App Sec Services
Our cloud sec and app sec services work towards making your organization “CyberImmune”
Cloud Pentesting and Configuration Review (CSPM)
Test and optimize your cloud configurations to prevent misconfigurations and unauthorized access.
Dynamic Application Security Testing (DAST)
Simulate real-world attacks to uncover and address security gaps in your applications.
Operational Technology (OT) / ICT Security
Secure operational and communication systems to ensure reliability and prevent disruptions.
Supply Chain Security (SCA)
Evaluate and secure third-party components to ensure a robust and trusted application ecosystem.
SAST and Secure Code Review
Analyze your code for vulnerabilities and ensure it adheres to secure coding practices.
Web & Mobile App Security
Protect your applications from vulnerabilities that could compromise user data and operational reliability.
Threat Modelling
Identify potential threats and risks early in the development cycle to mitigate them effectively.
DevSecOps / Secure SDLC
Integrate security practices into your development process for continuous, proactive protection.
API Security
Safeguard APIs from unauthorized access and ensure secure communication between applications.
How CyberImmune Secures Your Cloud Applications
Our comprehensive Vulnerability Management service ensures that security weaknesses are systematically and continuously identified, evaluated, treated, and reported on.

Identify Vulnerabilities
Perform in-depth assessments, including static and dynamic application testing, to uncover security gaps in your systems.

Tailored Security Strategy
Develop a customized security roadmap that aligns with your business needs, ensuring comprehensive protection.
Actionable Insights
Provide detailed reports with prioritized recommendations to enhance your application and cloud security posture.

Continuous Protection
Implement DevSecOps practices, monitor threats, and ensure secure software development throughout the lifecycle.
Why Choose CyberImmune?
Customized Solutions
Our services are tailored to your unique infrastructure and business needs.
Comprehensive Reporting
Reports include vulnerabilities, remediation steps, improving security posture.
Expert Team
Our experienced professionals bring in-depth knowledge to secure your cloud and apps effectively.
Remediation Guidance
Supporting clients fixing vulnerabilities, strengthening their security posture.
Comprehensive Coverage
From web apps to OT/ICT systems, we provide end-to-end cloud and application security services.
Proactive Approach
We identify vulnerabilities before they are exploited, helping you stay ahead of threats.
VAPT Tools and Technologies We Use
Our team of experts use the latest professional platforms and tools to perform the penetration tests and to secure your applications, network and cloud from all evolving threats.
Network Vulnerability Scanners
- Nessus Professional
- Qualys Vulnerability Management
- OpenVAS
Web Application Scanners
- BurpSuite Professional
- Acunetix
- OWASP ZAP
Mobile Application Testing Tools
- MobSF (Mobile Security Framework)
- Drozer (for Android)
- idb (for iOS)
API Testing Tools
- Postman
- SoapUI
- Insomnia
OT/ICS Security Tools
- Nmap NSE Scripts for ICS
- Shodan
- Dragos Platform
Cloud Security Tools
- Scout Suite (for AWS, Azure, GCP)
- CloudSploit
- Prowler (for AWS)
Compliance Checking Tools
- OpenSCAP
- Lynis
Code Analysis Tools
- SonarQube
- Veracode
- Checkmarx
Frequently Asked Questions
What is cloud and application security, and why do we need it?
Cloud and application security focuses on protecting your applications, data, and infrastructure in cloud environments. It helps prevent breaches, ensures compliance, and strengthens your overall security posture.
How does CyberImmune secure cloud applications in complex environments?
We provide tailored security strategies, including vulnerability assessments, penetration testing, threat modeling, and secure development practices, ensuring your cloud and applications are protected end-to-end.
What is CSPM?
CSPM (Cloud Security Posture Management) is a process that identifies and fixes cloud misconfigurations to ensure compliance, prevent data breaches, and maintain the overall security posture of your cloud infrastructure.
What are cloud security tools you use?
We utilize industry-leading tools such as Bright Security for DAST, SAST platforms for code reviews, and CSPM tools to monitor and secure cloud configurations across AWS, Azure, and GCP environments.
What is the difference between cloud pentesting and configuration review?
Cloud penetration testing (pentesting) simulates real-world attacks to identify security weaknesses, while configuration review (CSPM) evaluates and remediates misconfigurations in your cloud environment to meet compliance and security standards.
Do you perform AWS cloud penetration testing?
Yes, we specialize in AWS cloud penetration testing. Our assessments identify vulnerabilities, misconfigurations, and potential risks specific to AWS environments, ensuring robust cloud security.
How often should cloud and application security testing be conducted?
Regular testing—quarterly, bi-annually, or after significant updates—is critical to addressing evolving threats and ensuring your applications and cloud infrastructure remain secure.
What standards or compliance frameworks do your services align with?
Our services align with standards like ISO 27001, SOC 2, GDPR, HIPAA, and industry best practices, helping you achieve and maintain regulatory compliance.
How do you ensure the security of our data during testing?
We follow strict security protocols and confidentiality agreements. All testing is conducted by vetted professionals, and any sensitive data encountered is handled according to agreed-upon procedures.
Do you provide remediation support after the cloud and app security testing?
Yes, we offer post-assessment support to help interpret results and guide your team through the remediation process. We can also conduct re-testing to verify that vulnerabilities have been properly addressed.
What certifications do your professionals hold?
Our team includes professionals with certifications such as CCSP, AWS Certified Security, Azure Security Engineer, CEH, OSCP, CISSP, and other relevant industry qualifications. We ensure our team's skills are always up-to-date.
